
How does a VPN really work? To make your search for the best VPN provider a little easier, I will try to sum up some issues related to normal internet use and explain their importance in relation to your safety.
First of all you don’t need to be doing illegal stuff on the internet to make you want a VPN, as ordinary users have an even greater risk surfing the internet as they are not always aware of the tricks being used to steal information.
If you’re using Wi-Fi which you probably will, you’re more exposed to the outside world then when using cable-network. Reading a simple online-newspaper which shows you advertisements between the lines always establishes a connection with your IP-address just in order to show the images. Reading your emails which many times include images and links transfer your IP-adress to external servers filtering your behavior. To make it simple YOU’RE EXPOSED to the world. For all doing the wrong-illegal stuff on internet like downloading films and music there’s a simple warning. Stop doing what you do..or get fined …or get a VPN to make yourself invisible to the outside world.
Being invisible, is what all VPN providers claim, but are you really safe and protected ? No way…check :
- ipleak.net(IPv4, IPv6, WebRTC, and DNS)
- Perfect Privacy(based in Switzerland )
- ipleak.org (IPleak, DNS leak, WebRTC leak )
Any VPN which has its base location in the USA is not fully safe proof. They have to deal with severe law regulations regarding logging of users and there internet use. So the first thing you need is a provider NOT LOGGING any IP or online activity! Simple and safe.
HOW VPN WORKS
A VPN protects your privacy by creating a secure “tunnel” across the Internet between you and your Internet destination. This tunnel is created by first authenticating your client–a PC, tablet, or smartphone–with a VPN server. The server, which you can run yourself with programs such as OpenVPN, then uses one of several encryption protocols to make sure that everything sent between you and websites and Internet services can’t be monitored. It does this by creating an encrypted tunnel, which is like putting a package into a box and then sending it to someone. Nobody can see what it’s inside the box until it’s opened/decrypted.
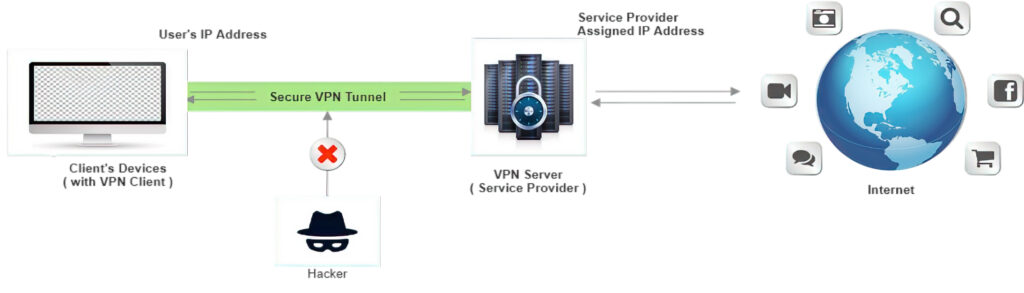
An encrypted VPN tunnel – image credit: Check Point Software.
These VPN protocols run as a lightweight server program. VPN providers run multiple VPN servers on virtual machines (VMs) or containers. This enables them to serve tens of thousands of clients from their data centers without spending a fortune on servers. You normally can’t choose which protocol to use within the VPN software itself, but you can certainly choose a VPN that offers one of the more secure protocols.
VPNs cannot make online connections completely anonymous, but they can usually increase privacy and security. To prevent disclosure of private information, VPNs typically allow only authenticated remote access using tunneling protocols and encryption techniques.
The VPN security model provides:
- confidentiality such that even if the network traffic is sniffed at the packet level (see network sniffer and deep packet inspection), an attacker would see only encrypted data
- sender authentication to prevent unauthorized users from accessing the VPN
- message integrity to detect any instances of tampering with transmitted messages.
Secure VPN protocols include the following:
- Internet Protocol Security (IPsec) was initially developed by the Internet Engineering Task Force (IETF) for IPv6, which was required in all standards-compliant implementations of IPv6 before RFC 6434 made it only a recommendation.[7] This standards-based security protocol is also widely used with IPv4 and the Layer 2 Tunneling Protocol. Its design meets most security goals: authentication, integrity, and confidentiality. IPsec uses encryption, encapsulating an IP packet inside an IPsec packet. De-encapsulation happens at the end of the tunnel, where the original IP packet is decrypted and forwarded to its intended destination.
- Transport Layer Security (SSL/TLS) can tunnel an entire network’s traffic (as it does in the OpenVPN project and SoftEther VPN project[8]) or secure an individual connection. A number of vendors provide remote-access VPN capabilities through SSL. An SSL VPN can connect from locations where IPsec runs into trouble with Network Address Translation and firewall rules.
- Datagram Transport Layer Security (DTLS) – used in Cisco AnyConnect VPN and in OpenConnect VPN[9] to solve the issues SSL/TLS has with tunneling over TCP (tunneling TCP over TCP can lead to big delays and connection aborts [10]).
- Microsoft Point-to-Point Encryption (MPPE) works with the Point-to-Point Tunneling Protocol and in several compatible implementations on other platforms.
- Microsoft Secure Socket Tunneling Protocol (SSTP) tunnels Point-to-Point Protocol (PPP) or Layer 2 Tunneling Protocol traffic through an SSL 3.0 channel (SSTP was introduced in Windows Server 2008 and in Windows Vista Service Pack 1).
- Multi Path Virtual Private Network (MPVPN). Ragula Systems Development Company owns the registered trademark “MPVPN”.[11]
- Secure Shell (SSH) VPN – OpenSSH offers VPN tunneling (distinct from port forwarding) to secure remote connections to a network or to inter-network links. OpenSSH server provides a limited number of concurrent tunnels. The VPN feature itself does not support personal authentication.[12][13][14]
Tunnel endpoints must be authenticated before secure VPN tunnels can be established. User-created remote-access VPNs may use passwords, biometrics, two-factor authentication or other cryptographic methods. Network-to-network tunnels often use passwords or digital certificates. They permanently store the key to allow the tunnel to establish automatically, without intervention from the administrator. (source: https://en.wikipedia.org/wiki/Virtual_private_network)